How Video Analytics Can Improve Access Control
Organisations around the world are heavily invested in monitoring and controlling access at their facilities—and for a good reason. Buildings can hold a fortune in sensitive information, valuable assets, and critical workloads. It’s a gold mine for malicious actors looking to profit from or disrupt your business. It’s why companies spend on access control cards and credentials, biometric & card readers, HID Mobile Access and other access control technologies.
There’s a fine line to walk, however, when it comes to access control. Organisations have to manage security and productivity, as the two are rival commodities. Time-consuming secure entry points and identification processes can help prevent breaches, but they can also increase costs and complexity.
Video analytics can be of help to organisations struggling to ensure their security and minimise the opportunity cost of strict compliance policies.
In this article, we’ll dive into how that works, and how it can benefit an organisation.
Authorisation at First Sight
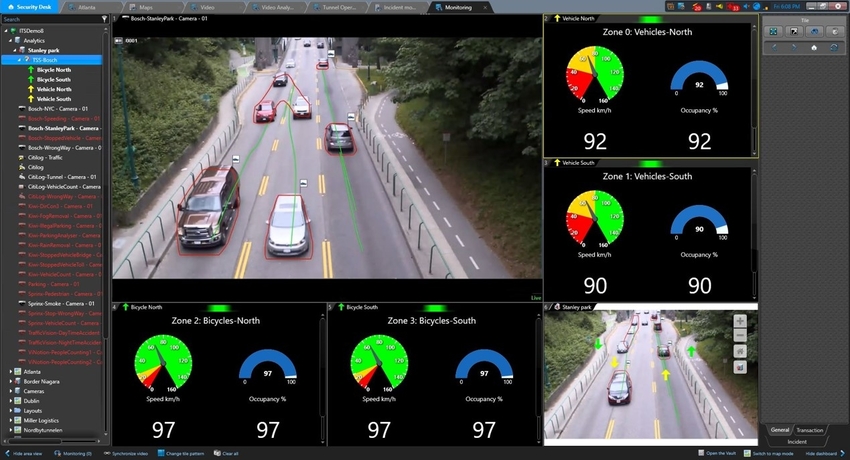
Video analytics, is computer vision (CV). The use of algorithms, trained against a data set (i.e. COCO or YOLO) to detect and classify objects including faces, people and vehicles.
In traditional settings, security staff operate an on-site control room and visually grant access based on whether a person is or isn’t authorised to enter. A visitor or employee might present identification, use a proximity or iCLASS smart card, use a HID Mobile Access credential on their phone or ensure their face is visible to the manual operator to prove that they’re who they claim to be.
Secure access is a perfect example of a positive use case, where all users are opted-in and consenting to being recognized. Selecting a facial recognition system that is low in bias will ensure a positive user experience and high-accuracy rate for all users of your face-based secure access system.
At its most basic video analytics uses grayscale image analysis to look for differences in pixels, to determine the edge of an object. : the latest developments in artificial intelligence (AI), machine learning, and object detection to automate the authorisation process.
It can do this in a number of ways:
1. Facial recognition
Facial recognition requires a users face to be preregistered into the facial recognition platform in order to provide high speed verification of the users face to provide contactless entry. By curating a database of images of employees, with varying levels of access, it’s possible to train a facial recognition system.
For any biometric solution, a quality template and biometric sample is key to achieving high accuracy and low false acceptance. Access control applications are likely to have even higher facial recognition accuracy rates than passive monitoring use cases due to cooperation of the subjects. Enrollment is performed in a controlled environment with opted-in subjects providing high quality reference images. When access control systems are set up, cameras are placed within a maximum distance from subjects to ensure optimal pixel density (on average twice that required for high accuracy recognition).
Performance with Facemasks With facemasks now a part of standard attire, it’s crucial that any face-based biometric solution
can detect and recognize even partially obscured faces. Facemasks reduce the amount of biometric information an algorithm can use to detect and correctly match a face. However, requiring a user to remove their mask at a secure access point introduces friction and increases the risk of virus transmission. Leading facial recognition providers understand this challenge and have invested in
training their algorithms to detect and recognize masked faces.
While facial recognition isn’t without controversy, it’s much easier to match images on a camera stream to images on a database than, say, categorising different types of people based on captured video.
Ethical Use & Reducing Bias
There is well known racial and gender bias in many facial recognition algorithms as confirmed by studies from NIST and other independent evaluators. These biases are a direct result of poor training data and bias within product development processes. Deep learning algorithms are only as smart as the data on which they are trained and it’s easy for developer bias to creep into algorithms if these unconscious biases are not addressed. That’s why it is critical to choose a facial recognition system that performs uniformly across faces of differing genders and skin tones and to commit to ethical use cases. Secure access is a perfect
example of a positive use case, where all users are opted-in and consenting to being recognized. Selecting a facial recognition system that is low in bias will ensure a positive user experience and high-accuracy rate for all users of your face-based secure access system.
Access control solutions based on facial recognition are a fast and efficient method for granting access to authorized personnel without the need for contact, and SAFR’s application is highly-accurate whether masks are being worn or not.
2. Number Plate Recognition
For properties with parking facilities, loading bays, or any other vehicle entry points, number plate recognition is an essential analytics application. By integrating number plate recognition with your access control system you can manage activity without impeding traffic flow. Using Genetec AutoVu™ SharpV number plate recognition cameras integrated into Genetec Synergis™, access control cameras can be managed like a door reader. You can assign access rights and schedules and restrict access at a moment’s notice. More importantly, your team is alerted when blacklisted or unknown vehicles enter the property. The outcome? Your staff has a more complete view of their environment and is able to act faster, without waiting until someone arrives at the front door. Beyond keeping an automated and dynamic record of visitors’ number plates, your security cameras can be set to approve or deny vehicular access to certain areas without the need for HID prox or iCLASS cards or delegated staff.
The technology can be used in tandem with smart parking monitors and other IoT solutions to improve traffic flow and enforce parking restrictions. Think of it as an added bonus on top of more streamlined security.
3. Custom Rules for Access
In some cases, access rules can be dynamic. Certain floors or offices may be open to visitors and employees during business hours but closed at other times of the day. Because access monitoring depends on the alertness and vigilance of your security teams, video analytics can be very useful in sending notifications or prioritising views of protocol violations as they happen.
This eliminates room for human error in control rooms by detecting human movement in areas that should be vacant and ensuring that the people watching over your facilities know about it ASAP.
A Few Notes on Implementation
These and other video analytics usage cases shouldnt be used as stand-alone methods for access control. We stress the importance of having multiple layers of verification to ensure the safety and security of your building and the assets and people within.
And as we mentioned at the top of this article, it pays to be deliberate when designing your compliance policies. You want to make sure that your policies don’t sacrifice security for convenience, but rather balance the two. Layers including cards, readers, cameras, and in select cases, security personnel must be used alongside video surveillance systems to ensure the best outcomes.
Open a dialogue with your facility’s stakeholders to determine which points of entry are disruptive to their daily workflows, and use technology to ease the burden. Security is a holistic undertaking, after all.
Finally, be sure to partner with a security system provider that understands the technology and its limitations. Security systems are only as good as the people who wield them, and the same is true when it comes to automation. Human insight continues to drive outcomes when using artificial intelligence — the robots haven’t taken over just yet.
Conclusion
Access control doesn’t have to be a labyrinthine nightmare of card-swiping and logbook-signing. The best operating procedures ensure security without wasting hours a year to verification. Video analytics can provide a layer to your security fabric that makes security clearance as easy as showing up to work.
We highly recommend that organisations explore the benefits of video analytics. There is a broad range of use cases where the technology can prevent losses, speed up investigations, and unearth insights about your organisation and its patrons.
JD Security specialises in the latest and most powerful security tools on the market. We select our employees for their veterancy as well as their adaptability to emerging threats and solutions—and we train them to serve your visitors as well as you train yours.
Call us on 1300 556 334 or email [email protected] to learn how you can benefit from our solutions.
Customers in New Zealand call 0800 345 677 or email [email protected].
Latest Posts
Comments are closed.